infoTECH Feature
The Importance of Password Managers and MFA in your Security Stack
 By Special Guest
By Special GuestCory Mathews, , Offensive Security Technical Lead, Sr. Adversarial Engineer, Section8-Critical Start

The subject of password strength and complexity requirements has been discussed and debated ad nauseam in the security industry. It’s a subject as old as information security and will not be going away any time soon.
Penetration testers love passwords because they can be abused to achieve the objectives of a client’s assessment. Malicious actors also love passwords, many of the mass phishing campaigns seen in the wild have the sole objective of harvesting credentials from gullible users.
But what happens when you don’t find passwords written down on post-it notes attached to your monitor? This is where cracking password hashes comes in to play.
There are numerous methods to obtain hashed credentials whether it is from capturing a WPA handshake on your Wi-Fi, passwords stored in a database within an application, or capturing Windows domain credentials passing over a corporation’s network. Whatever your method, the take-away is your super-secret password may not be as safe as you think.
Critical Start’s penetration testing team Section8 routinely crack password hashes during client assessments using a purpose-built server with 8 Nvidia Titan V graphics cards.
On the software side, an industry favorite is the password recovery tool hashcat. During penetration testing engagements, this hardware and software duo enable assessors to quickly and efficiently crack captured password hashes on the fly.
A common source of domain credentials abused by red teamers and malicious actors alike are Windows NTLMv2 hashes captured from the network. These hashes are from a challenge-response authentication protocol that Windows clients use to authenticate to other Windows servers like network shares.
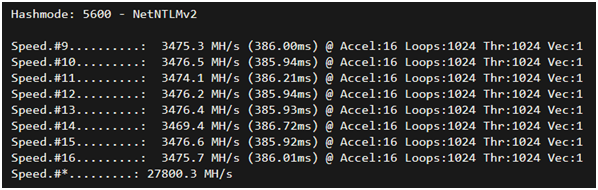
To put it simply, this system can crack hashes at over 27.8 billionguesses per second.These hashes are the more cryptographically “strong” method employed within a Windows environment, but what about weaker algorithms?
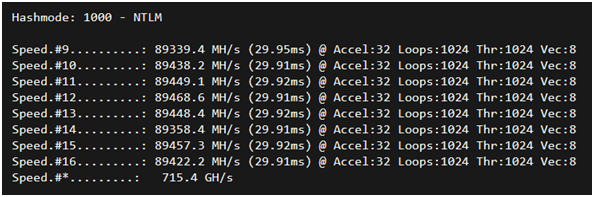
A common post-exploitation step for a penetration testing team is to obtain a copy of the Windows Active Directory database file NTDS.dit. This file stores user credentials in an older and weaker algorithm simply called NTLM. These hashes are even easier to crack.
NTLM hashes dumped from Active Directory are cracked at a rate of over 715 billion guesses per second. It is shocking how often we see passwords of 8 or fewer characters still in use today. Cracking hashes of passwords 6 characters or less are almost instant and 7 characters take about 4 minutes. The difficulty and time required to crack hashes is an exponential increase as the character length of passwords increments. For instance, a 9-character brute-force requires approximately 24 days. Increasing to a length of ten or beyond will create issues if using the full keyspace, as it is way too large for hashcat to handle and will error out before attempting to crack.
At this point, organizations may be thinking, “Our policy requires a minimum length of 10 with numbers and special characters so we are safe!” To that, we say hashcat has features beyond raw brute-forcing. These features allow a wordlist or dictionary to be used along with a “rule” file. A single rule can take a single word from a dictionary and use it as a seed to create multiple permutations. An example would be taking the base word ‘password’ and replacing some characters with numbers like passw0rd, p4ssw0rd, pa55word, etc. While that can help with complexity, other rules will take 2 or more entries from a list and concatenate them to create longer passwords (e.g. correcthorsebatterystaple).
With large wordlists and complex rules, password candidate lists can be created that contain quadrillions of unique entries. Using a wordlist that is roughly 20 GB (about 1.1 billion entries) along with a file with 310,372 individual rules will create over 335 trillion unique passwords to guess. The real kicker is that running a cracking session with those options against a list of NTLM hashes takes roughly 45 minutes to complete.
Inevitably there will be plenty of passwords that can’t be cracked in a given collection of hashes, but if a team can crack 70-80% of passwords in an environment, it may be time to take a hard look at authentication policies within your organization.
Yes, that is a lot of doom and gloom. What steps can you take to defend your organization against a group of malicious actors that now have your passwords in plain text? The answer is the same as in all security: defense-in-depth.
One step is to limit or remove the human element from password creation using a password management solution. Humans have and will always be one of the weakest links when it comes to security. A password manager helps eliminate password re-use across multiple accounts as well as creating longer and more complex passwords without the individual having to remember each one for each account. There are numerous password managers on the market ranging from freeware, open-source applications, all the way to enterprise-grade solutions.
Another is implementing multi-factor authentication (MFA (News - Alert)) solutions for any and all applications or systems that support it. While not totally infallible, MFA solutions offer an added layer of complexity to a malicious actor’s attack chain that is often a decent deterrent from them pursuing further action. These solutions can also serve a canary function, alerting users that their credentials are being used by someone other than them.
As with everything in security, and life in general, there is no single “silver bullet” that will protect you and your organization. However, layering security and taking steps to identify and mitigate authentication policy shortcomings is one of the many ways to improve your organization’s security posture.
Cory Mathews is Offensive Security Technical Lead, Sr. Adversarial Engineer of theSection8team at Critical Start, MDR experts and developer of a cloud-based, SOAR platform that resolves 99% of security events.
.
Edited by Maurice Nagle
infoTECH Headlines
What Is AWS EFS? Features, Use Cases, and Critical Best Practices
Cost-Effective Approaches to s1000d Conversion
A virtual crossroads for technology enthusiasts
Benefits of employee monitoring software in preventing overworking of workers
CI/CD: Trends and Predictions for 2024
Technical Documentation for IT: A Practical Guide
Managing Your Costs on AWS: A 2024 Guide
What Is Application Dependency Mapping?
Top 5 Kubernetes Errors and How to Solve Them
How Artificial Intelligence Can Improve the World of Online Gaming Platforms
Rich Tehrani
Rich Tehrani




