infoTECH Feature
Vectra Networks Report Reveals What Attackers Do Once Bypassing Perimeter Defenses
The headlines are filled with a now constant drumbeat of data breaches. Post mortems on such events tend to focus on who was responsible, how long it took to discover and remediate the situation and how they accomplished their exploit. What typically does not get covered is what happens once the bad guys bypass your perimeter, i.e., can go undetected.
Seeking to shed more than a little light on the subject, San Jose, CA (News - Alert)-based Vectra Networks, a provider of real-time detection of in-progress cyberattacks, is out with the first edition of The Post Breach Industry Report. As the report notes, there has been no shortage of security reports that detail the multitude of threats seen by perimeter and endpoint defenses, such as firewalls, intrusion prevention systems, sandboxes and antivirus software. However, they can rightfully claim that this is the first report, using real-world data from the Vectra X-series platforms currently in production networks, that reveals what attackers do within a network once they evade perimeter defenses.
The report collected data over five months from more than 100,000 hosts within sample organizations. While the numbers obviously are not as large as those documenting attacks on perimeter defenses they are nonetheless disturbing. In fact, the study found that:
- More than 11,000 hosts experienced one or multiple cyberattacks that made it through perimeter defenses.
- Of these attacked hosts, 10 percent had detections for two or more attack phases – such as botnet monetization, command and control, reconnaissance, lateral movement and exfiltration.
- Overall, 15 percent of hosts in the participating organizations experienced a targeted attack.
- Even for attacks that reached the exfiltration phase, organizations had two or more opportunities to stop the attack prior to significant data loss.
The study revealed, as noted in the second item, that once the attackers got in they performed reconnaissance via internal port scans, lateral movement using brute force attacks, remote control of the attack with command and control communication, and exfiltration through hidden tunnels. In short, attackers have a lot of tools in their tool kits for wreaking havoc.
I had the opportunity to speak with Vectra Networks CTO, Oliver Tavakoli and Mike Banic (News - Alert), VP Marketing about the findings. There was the obvious bad news, but also some good news.
First that bad news, as Tavakoli explained, “We found that the majority of attacks are opportunistic is nature. Those with malicious intent are trying to make money from somebody and are constantly seeking a vulnerability to gain access. Despite the headlines, targeted attacks are less frequent.”
He added, “Cyberattacks are increasingly sophisticated, highly organized, and successful despite $60 billion invested in cybersecurity annually worldwide. All of the attack phases detected in this report are ones that evaded organizations’ perimeter and endpoint security systems.”
That taxonomy of attack phases is actually important to consider. As Banic noted, “Attackers who evade perimeter defenses, if they are not employees do not know a lot about your network. They need time to explore and understand it. This means if you are being attacked and you have time to analyze what is going on.”
This is where the Vectra X-series with its real-time detection of attack phases comes in. As Banic explained, it looks at critical east/west traffic instead of the typical concentration on north/south where defenses are aimed at the barbarians storming the gates.
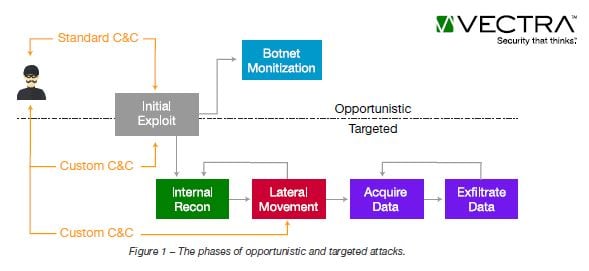
Two graphics from the report are useful. The first is a nice illustration of the phases of opportunistic and targeted attacks.
(click to enlarge)
The report provides granularity on how and why opportunistic attacks are more frequent than targeted ones, 85 percent vs. 15 percent. It also details the different types of Command and Control detections, which in many ways are the keys to the enterprise in terms of causing real damage. It also goes into detail about the frequency of the dreaded botnet attacks breaking them by type; the frequency of Darknet vs. Port Scan detections for reconnaissance; and the frequency of Lateral Movement detections by type.
What struck me in my discussions with the Vectra executives was their solution’s ability to provide what amounts to a narrative about the nature and progress of detections as seen in the below. In fact, the below is actually a worse-case scenario for when an attack is targeted.
(click to enlarge)
It is not a pretty picture, but it is interesting in terms of watching the progression and associated probabilities that can be valuable to IT security professionals.
The report explains the timeline and what concerns it should raise. It also highlights a message that should be interpreted as good news, which Tavakoli stressed. “This is like the Rolling Stones song ‘Time is on My Side.’ If you are watching, time is on your side. The idea is to connect the dots as quickly as possible. It is important to remember that attacks take cognition and thinking by attackers.”
The other message here is that visibility is critical. This may be obvious when it comes to all of those tools for watching the perimeter. It should become equally as obvious for watching that east/west traffic so that activities that bypass the perimeter and pose high risks to the business do not go undetected and can be remediated quickly.
All security professionals know there is no silver bullet when it comes to managing business risks posed by the increased complexity of today’s connected world. However, they will also tell you that they can’t defend against what they don’t know, and knowing what is going on behind the fire-wall in real-time is an area where knowledge is power.
Edited by Maurice Nagle
infoTECH Headlines
What Is AWS EFS? Features, Use Cases, and Critical Best Practices
Cost-Effective Approaches to s1000d Conversion
A virtual crossroads for technology enthusiasts
Benefits of employee monitoring software in preventing overworking of workers
CI/CD: Trends and Predictions for 2024
Technical Documentation for IT: A Practical Guide
Managing Your Costs on AWS: A 2024 Guide
What Is Application Dependency Mapping?
Top 5 Kubernetes Errors and How to Solve Them
How Artificial Intelligence Can Improve the World of Online Gaming Platforms
Rich Tehrani
Rich Tehrani



 By
By