infoTECH Feature
Survey Finds IT Security Pros are Aware of Data Breaches Not Disclosed by Their Employers
The headlines almost daily scream about enterprise security data breaches. Clearly, we are under attack. The question that arises is whether the community at large knows just how pervasive and pernicious those attacks are?
Advanced Persistent Threats (APTs) solutions provider, Clearwater, FL-based ThreatTrack wanted to get more visibility into what is transpiring in U.S. enterprises regarding their work fending off malware threats and in October of this year had research firm Opinion Matters survey 200 individuals on the front lines of cyber security to get a better handle on things. There is good news and bad news in their findings.
Let’s begin with the bad news. The survey found that 57 percent of enterprise malware analysts have investigated or addressed a data breach that was never disclosed by their company. As ThreatTrack points out, these results suggest that the data breach epidemic – totaling 621 confirmed data breaches in 2012, according to Verizon’s 2013 Data Breach Investigations Report – may be significantly underreported. Equally as disturbing is that companies with more than 500 employees are more likely to have had an unreported breach, with 66 percent of malware analysts with enterprises of that size reporting undisclosed data breaches.
The study, Malware Analysts Have the Tools to Defend Against Cyber-Attacks, But Challenges Remain, highlights several other challenges now confronting enterprise cybersecurity professionals.
Outmanned, Outgunned and Out of Time
The sub-head above highlights the problem. In fact, despite survey results that show the pros by and large believe they have the tools to protect their organizations’, 40 percent of respondents reported they are hampered by not having enough highly-skilled security personnel on staff. In addition, it also found that making matters that much more challenging is the amount of time they spend handling easily avoidable malware infections generated by their C-levels. The list of such C-level caused infections should give everyone pause and includes:
- Visiting a pornographic website (40 percent)
- Clicking on a malicious link in a phishing email (56 percent)
- Allowing a family member to use a company-owned device (45 percent)
- Installing a malicious mobile app (33 percent)
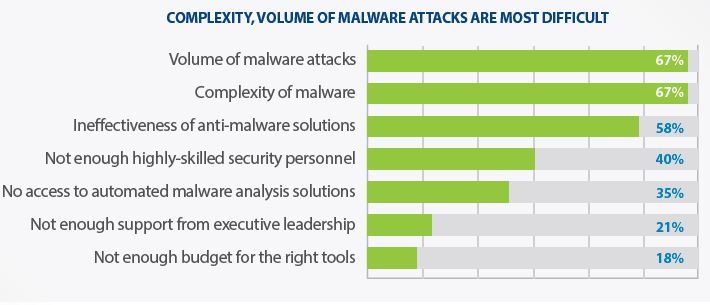
As the graphic below details, when asked to identify the most difficult aspects of defending their companies’ networks from advanced malware the volume and complexity topped the list.
Source (News - Alert): ThreatTrack Report, Malware Analysts Have the Tools to Defend Against Cyber-Attacks, But Challenges Remain
The pullout here is that 35 percent said one of the most difficult aspects of defending their organization from advanced malware is the lack of access to an automated malware analysis solution, which cuts analysis times to just minutes.
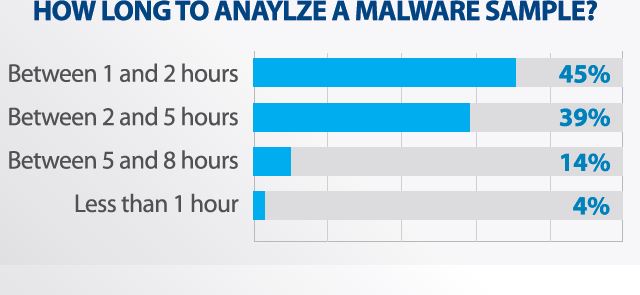
Another chart from the study worth noting is on the time it takes to analyze a malware sample. The short answer, given the need to rapidly mitigate the risk, is it takes longer than it should.
Source: ThreatTrack Report, Malware Analysts Have the Tools to Defend Against Cyber-Attacks, But Challenges Remain
In answer to a question about their opinion on country of origin for attacks launched against their networks and the highly topical subject of government-sponsored cyber espionage. The answers confirmed what has been in the news with 37 percent of respondents said the U.S. is the country most adept at conducting cyber espionage and China coming in a close second at 33 percent.
As stated above, there was some good news in the survey. It came in the form of the finding that respondents believe their ability to defend against malware and other cyber threats has improved over the past year.
- 38 percent said it’s gotten easier to defend their company’s network from cyberattacks
- 27 percent said it has become more difficult
- 35 percent stated it is about the same
In comments about the study, ThreatTrack CEO Julian Waits, Sr. noted that: “While it is discouraging that so many malware analysts are aware of data breaches that enterprises have not disclosed, it is no surprise that the breaches are occurring…Every day, malware becomes more sophisticated, and U.S. enterprises are constantly targeted for cyber espionage campaigns from overseas competitors and foreign governments. This study reveals that malware analysts are acutely aware of the threats they face, and while many of them report progress in their ability to combat cyber-attacks, they also point out deficiencies in resources and tools.”

image via shutterstock
The study reinforces others that have come out recently about the transforming nature of cyber attacks and IT’s ability to keep up with the bad guys. The recurring theme is obviously that the sophistication and frequency of attacks is growing. However, other important observations include: the need for greater visibility across all potential vectors of attack; having the right tools in the right hands to identify and remediate problems quickly; and more investment in obtaining the right tools and more staffing who have the skills to use them.
The last common theme has been the need for education, education, education. This is not the first study to identify C-levels as a major cause of malware infection. Unfortunately, it is not likely to be the last. Realities are that C-levels are increasingly running their enterprises from their tablets and smartphones, and while digitally adept in the use of the devices are not as adroit in understanding or doing something about how risky such use can be when attention is not paid to even basic protection best practices.
Other studies have noted that there is an increasing breakdown in trust between IT and end users, particularly Gen X and Y users who believe convenience trumps following organization policies and rules on accessing and using their favorite online capabilities. What all of the studies seem to point to is that a culture of protection needs to be put in place with penalties that deter risky behavior and that a reasonable place to start is having the top of the company set the right examples and send the appropriate messages about what will and will not be tolerated.
This is much more than an IT problem. In fact, as the study notes, IT believes its ability to defend is improving and the tools are available to enable them to provide better protection, however, they are going to need help in the form of cooperation. Awareness needs to translate into measurable improved risk management results.
Here in the U.S. there was an old TV commercial for a muffler repair company whose tag (News - Alert) line was, “You can pay me now, or pay me later!” With malware risks on the rise, the relevance of pay me now so I do not suffer the consequences is a tag line that security vendors can and should reinforce.
Edited by Ryan Sartor
infoTECH Headlines
What Is AWS EFS? Features, Use Cases, and Critical Best Practices
Cost-Effective Approaches to s1000d Conversion
A virtual crossroads for technology enthusiasts
Benefits of employee monitoring software in preventing overworking of workers
CI/CD: Trends and Predictions for 2024
Technical Documentation for IT: A Practical Guide
Managing Your Costs on AWS: A 2024 Guide
What Is Application Dependency Mapping?
Top 5 Kubernetes Errors and How to Solve Them
How Artificial Intelligence Can Improve the World of Online Gaming Platforms
Rich Tehrani
Rich Tehrani



 By
By