infoTECH Feature
'Exploit Kits are the Latest Weapons of Cyber Destruction' Warns Security Expert
Chris Larsen, Malware Research Team Leader at Blue Coat
Malware is a business; people make their living writing and distributing it. Exploit kits are an effective and streamlined methodology of distributing malware; they allow the ‘Bad Guys’ to distribute payloads at a higher level than we have seen in the past. For this reason we've seen exploit kits grow in popularity over the last few years.
Chris Larsen, Malware Research Team Leader at Blue Coat (News ![]() - Alert) gives his insight into the dark side of exploit kits:
- Alert) gives his insight into the dark side of exploit kits:
Exploit kits are a cheap [well, they used to be...] and effective platform to distribute malware to thousands of computers a day. In simple terms, exploit kits are prepackaged Web application software, designed to exploit visitors' computers with an array of attacks. If vulnerability is found on the visiting computer, any desired payload can be installed. These payloads can be any flavor of malware: from fake AVs and ransomware, to banking Trojans, and anything in-between. For a sometimes hefty price, one may obtain a subscription to one of these kits, host it on a Web server, and watch as innocent visitors are exploited and infected with malware.
For the last few years, the “king” of exploit kits has been the Blackhole Exploit Kit (BHEK), created by a group led by “Paunch” in Russia. This kit has been a leader in the industry for a long time, but with the rapid growth of the malware industry, several other exploit kits are competing for Blackhole’s customers.
Two of these are the "Sweet Orange (News - Alert)" kit and the Cool Exploit Kit that Blue Coat has been tracking for the last few months.
Forbidden Fruit
Sweet Orange comes to the market with many of the key features we have seen in other exploit kits: a database backend that records successful infections, statistics about exploits for Java, PDF, IE and Firefox, and of course regular updates. It does add a few unique selling points: a small footprint, a higher infection rate, and the claim that they will drive 150,000 unique visitors to your site daily.
150,000 unique visitors daily. Let’s look at what that means.
Let’s say that I want to create a botnet with a piece of malware that I write. Sweet Orange claims to get a successful infection rate of 10 percent to 25 percent of the visitors who land on the malicious webpage. (Many hacker forums claim it to be more like 10 percent to 15 percent.) If we go with the lower percentage, and I get my promised 150,000 unique visitors a day, that gives me around 10,000 infections a day. That’s 10,000 new computers a day that will be joining my botnet.
And it's all completely automated.
Cool Kit – Don’t let the name fool you
Cool kit is very similar to other exploit kits, but particularly similar to BHEK. This has led to speculation that Cool was developed by the same group.
Yesterday, Brian Krebs confirmed that Cool does indeed come from Paunch and his group -- his research led to posts on underground hacker forums where Paunch takes credit for Cool and gives some details on the project.
So what makes Cool different from BHEK and other exploit kits? For one, the Cool kit comes with a price tag (News - Alert) of $10,000 a month. That is significantly higher than BHEK and other exploit kits, that can run anywhere from $500 - $1,500 a month. The reason for the price hike apparently comes from a $100,000 investment into new exploits the developers announced, that will be used exclusively by Cool and not made public. This could give Cool a significant leg-up on the competition with other exploit kits.
Recently, I have seen a sharp increase in the amount of servers that are hosting the Cool kit. I wanted to do a comparison to see how the Cool traffic compares to the traffic we are seeing from Blackhole, so I went back and looked at the number of new servers my Blue Coat team submitted to Blue Coat's Malnet Tracker each month:
Notes:
- For simplicity, I'm using the number of unique IP addresses as a proxy for the number of servers.
- All the numbers represent new servers, not a cumulative total. (There would be a lot more BHEK servers in a cumulative model.)
- I use a starting value of zero in October; we hadn't decided that we were seeing a new exploit kit yet.
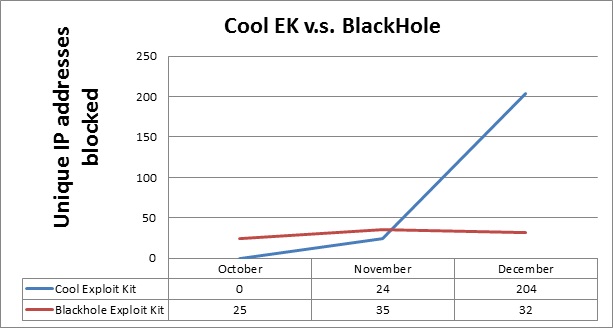
As you can see in the graph above, Cool began steadily gaining ground on Blackhole when it was released. Then in December, the number of new IP addresses skyrocketed -- Cool outgrew BHEK by 6 to 1.
We have also seen a couple of large IP subnets that are hosting a mix of Blackhole and Cool exploit kit sites. One network in particular is monstrous, and I incorporated it into the next chart:
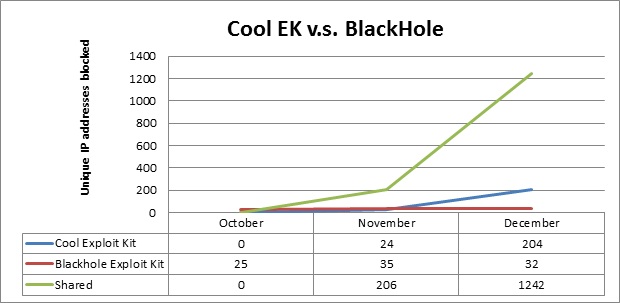
As you can see, the servers in the mixed-kit network greatly outnumber the servers that are hosting solely one type of exploit kit. From a high level perspective, it looks like most of them are hosting the Cool kit (which would make Cool's rise to power even more impressive).
Tracking Icebergs – Blue Coat’s WebPulse to the Rescue
So what do you do when there's a new exploit kit wreaking havoc? You investigate it.
There are some great resources to learn about Sweet Orange, and some will even tell you domains and IP addresses that are hosting it. One such resource is the Malware Domain List.
As of now, malwaredomainlist.com has seven IP addresses, and eight domains, that are known to be hosting Sweet Orange. That seems like a small number to be driving 150,000 unique visitors to your malware site a day.
So that's a good start, but it doesn't let us see the whole picture -- only the tip of the iceberg.
Thanks to WebPulse, and the amount of traffic that comes through each day, Blue Coat can see a lot more of the iceberg. In my research, I found 45 different IP addresses (and a total of 267 different domains) that are dedicated to Sweet Orange. This sounds a lot more in line with the claim of 150,000 unique daily visitors.
I wondered if anyone else was seeing these. To find out, I took a sample of 20 domains and 20 IP addresses (that were completely dedicated to Sweet Orange) and ran them through a couple of different public virus scanners.
Only seven of the 20 domains were caught by any of the vendors on Virustotal: three by one vendor, and four by another, or an average of 0.35 hits per domain. It got worse when I checked the IP addresses. There were zero hits on any of the 20.
I did the same test on URLVoid.com with the 20 domains. The tools there did a little better, averaging 1.25 hits for each domain. This is definitely an improvement, but it is still only the tip of the iceberg.
If that weren't enough to worry about, malicious sites move a lot faster than icebergs, changing IP address and domains to avoid detection. Blue Coat’s WebPulse’s malnet tracker can follow the malicious hosts wherever they go, protecting customers along the way -- we don't want them to be part of the "150,000.”
Edited by Rachel Ramsey
infoTECH Headlines
What Is AWS EFS? Features, Use Cases, and Critical Best Practices
Cost-Effective Approaches to s1000d Conversion
A virtual crossroads for technology enthusiasts
Benefits of employee monitoring software in preventing overworking of workers
CI/CD: Trends and Predictions for 2024
Technical Documentation for IT: A Practical Guide
Managing Your Costs on AWS: A 2024 Guide
What Is Application Dependency Mapping?
Top 5 Kubernetes Errors and How to Solve Them
How Artificial Intelligence Can Improve the World of Online Gaming Platforms
Rich Tehrani
Rich Tehrani




