infoTECH Feature
Continuous Database Monitoring is Key to Reducing Risk of National Retailer Breaches
When looking for the latest information and insights on cybersecurity, particularly data breaches, the Ponemon Institute is a terrific more than reliable source. Given what seems like an epidemic of U.S. retailers having customer data and other critical information compromised, Ponemon’s latest research, done in conjunction with database security behavioral analysis experts DB Networks, technology in the field of database security , “The SQL Injection Threat & Recent Retail Breaches“ report, is going to be must reading.
The survey findings are a page-turner on two fronts. In the first instance, the research does a good job of painting the landscape regarding the recent spate of cyberattacks on U.S. retailers. It should serve as a call to action to those in the space, specifically when it comes to protection of their SQL databases. Secondly, there are also recommendations about how not to be the next victim of a malicious SQL injection attack which the research found to be the most common means for bad guys to do bad things.
As the authors note, the SQL Injection Threat & Recent Retail Breaches“ report was conducted to gain a deeper insight into the recent U.S. retailers breaches, including to better understand:
- Why these retailers were so vulnerable
- What security countermeasures could have been employed
- Who was likely responsible for the attacks.
It analyzes responses from 595 IT security experts in the U.S. representing a broad spectrum of industries as well as the public sector. And, as the authors note, the study respondents are very familiar with the security compliance requirements for retailers who accept payment cards. In particular given the headlines, 69 percent of the respondents indicated their organization must comply with Payment Card Industry Data Security Standard (PCI (News - Alert) DSS).
“While details of the recent retailers breach haven’t yet been fully disclosed by the retailers who were breached or the U.S. Secret Service in charge of breach investigations, this study offers some interesting industry insight into these events from IT security professionals and experts familiar with PCI DSS,“ said Dr. Larry Ponemon, founder and chairman of the Ponemon Institute (News - Alert).
You can’t protect against what you don’t monitor
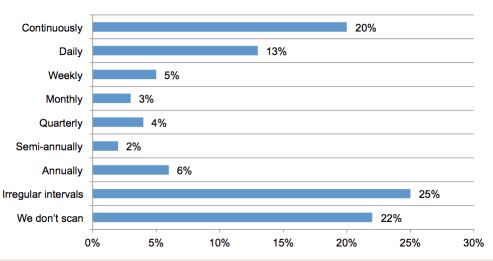
Before getting into the granularity of the survey results, the reason this subject should raise red flags can be seen in the graphic below which is the responses to the question, “How often does you company scan for active databases?”
Source (News - Alert): The SQL Injection Threat & Recent Retail Breaches Report, 2014
In short, if you are not watching or a only passively engaged you are heading for potential problems if you have not experienced them already.
Some of the key findings in the study include:
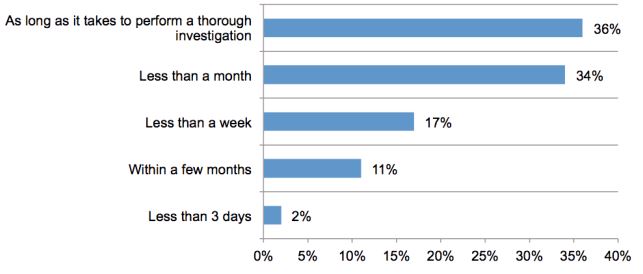
- Fifty-three percent of respondents indicated that breach notification should occur within a month.
- Initial reports were that a Russian teenager was the perpetrator of the Target (News - Alert) breach, however half the respondents felt that it was actually the work of a cybercriminal syndicate. Only 15 percent responded that a lone wolf hacker was the likely culprit, while 11 percent responded that nation-state actors were likely responsible.
- While most respondents believed that the attacks against the retailers databases involved SQL injection, almost half of the respondents said the SQL injection threat also facing their own organization is very significant.
- 64 percent felt their organization presently does not have the technology or tools to quickly detect SQL injection database attacks.
- As seen above, only one-third of respondents either scan continuously or daily for active databases. However, 25 percent reported they scan irregularly and 22 percent do not scan at all.
- Only 48 percent of respondents indicated that they test or validate third party software to ensure it’s not vulnerable to SQL injection.
- Forty-four percent utilize professional penetration testers to identify vulnerabilities in their IT systems; but 65 percent of those penetration tests do not include testing for SQL injection vulnerabilities
“It’s well known that database breaches, including these high-profile attacks against the retailers, are devastating to merchants in terms of lost sales and damage to their reputation,“ said Brett Helm, Chairman and CEO of DB Networks. “This study sheds additional light on the likely attack chain so that all retailers can now be more prepared in the future.”
In discussing the report with Dr. Ponemon he was quick to say, “What is surprising is that the vulnerability of SQL databases to injections by those with malicious intent is nothing new. In fact, there is software unfortunately available that would enable a 12 year-old to drain your database. It is why we are recommending continuous monitoring and were dismayed by the lack of frequent monitoring or lack of monitoring completely that retailers are presently doing.”
In fact, when those on the front lines were asked about how preset to provide protection of critical information, as can be seen below continuous monitoring of the database network along with advanced activity monitoring and encryption, topped the list.
Source: The SQL Injection Threat & Recent Retail Breaches Report, 2014
Dr. Ponemon also pointed to a finding that is a subject for those of you who follow my postings on security breaches have read rants on before, “When should victims be notified of a data breach?” Dr. Ponemon said, “This is an interesting question since there are dangers in being out with bad information if you act hastily, but as a matter of trust those impacted need to know, along with what steps they need to take if any, and they need know sooner rather than later. Transparency is the best policy, but it does need to be based on obtaining a certain level of knowledge which is why solutions such as DB Networks are so valuable.”
Source: The SQL Injection Threat & Recent Retail Breaches Report, 2014
What is clear from the report, as has been a trend in much of the recent security reports dealing with other types of cyberattacks, is that doing nothing more than just staying alert with real-time visibility into your environment, along with having the analytics and remediation tools to be both proactive and reactive, can go a long way to reducing risks. For retailers, whose lifeblood is those SQL databases, the report should serve to create a sense of urgency about fending off SQL injections.
For everyone else, that is great advice too, along with the desirability of keeping those who have been impacted informed with the best information possible and in a timely manner.
Edited by Maurice Nagle
infoTECH Headlines
What Is AWS EFS? Features, Use Cases, and Critical Best Practices
Cost-Effective Approaches to s1000d Conversion
A virtual crossroads for technology enthusiasts
Benefits of employee monitoring software in preventing overworking of workers
CI/CD: Trends and Predictions for 2024
Technical Documentation for IT: A Practical Guide
Managing Your Costs on AWS: A 2024 Guide
What Is Application Dependency Mapping?
Top 5 Kubernetes Errors and How to Solve Them
How Artificial Intelligence Can Improve the World of Online Gaming Platforms
Rich Tehrani
Rich Tehrani



 By
By