TMCnet News
Agari Uncovers National BEC Check Fraud RingFOSTER CITY, Calif., Feb. 20, 2020 /PRNewswire/ -- Agari, the market share leader in phishing defense solutions for the enterprise, announced today the results of an ongoing investigation by its Agari Cyber Intelligence Division (ACID) into a threat actor group which built an intricate network of check mules that has bilked thousands of companies.
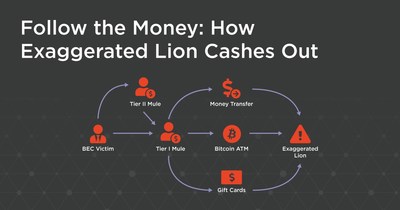
Dubbed Exaggerated Lion, the threat actor group is distinct from typical cybercriminal organizations in two ways. First, it uses physical checks to cash out money pilfered through business email compromise (BEC) attacks. For comparison, the Agari Q1 Email Fraud and Identity Deception Trends report found gift cards (62%) were the preferred cash-out method in most BEC scams, followed by direct transfers (22%) and payroll diversion (16%). And second, unlike most other BEC rings that are centrally located in Nigeria, the Exaggerated Lion actors are spread around multiple countries in Africa, including Nigeria, Ghana, and Kenya. Exaggerated Lion targeted more than 3,000 individuals employed by nearly 2,100 companies in BEC attacks between April 2019 and August 2019. The activity observed by ACID during this time period does not reflect the totality of Exaggerated Lion's target set, but does provide insight into where their preferred targets are located. It also clearly shows the far-reaching tentacles Exaggerated Lion has in the U.S. business world. If your company has more than 1,000 employees and you want to know if it is on the Exaggerated Lion hit list, please contact us at [email protected]. A vast majority of the employee targets identified held an "accounts payable" title, indicating the finance organization at businesses is under siege and needs to be extra diligent aout payment requests that come in from email. The use of keywords in an employee's title is a common way BEC groups quickly identify targets that are likely to handle transactions cybercriminal organizations are trying to exploit. Exaggerated Lion's search terms clearly included "accounts payable." The "low tech" use of physical checks to cash out from email phishing scams requires higher sophistication in social engineering techniques to dupe companies out of money and trick everyday folks into helping (often unwittingly). Since at least 2017, Exaggerated Lion has built a network of trusted "mules," people who they could rely on to deposit checks into bank accounts with few questions asked. Most of these mules were initially victims of Exaggerated Lion's romance scams, but as they were slowly groomed and a solid foundation of trust was developed, they were converted into mules who would receive illicit checks under the auspices of helping receive a large inheritance and pass the proceeds to Exaggerated Lion actors without question. It is important to note that most of the mule bank accounts were legitimate, making this scam almost undetectable through the usual anti-money laundering controls banks have in place to detect suspicious activities. Agari has uncovered the identities and locations of 28 check mules that were used in Exaggerated Lion's scams. In October 2019, one of Exaggerated Lion's most trusted mules was arrested. This is a situation where the romance victim-turned-money mule was aware that he was participating in illicit activities. Exaggerated Lion uses G Suite to maximize the amount of potential emails they can send in a day. With standard Gmail accounts, the most common free webmail provider used to send BEC attacks, a user can only send a maximum of 500 messages a day. Once a G Suite account is out of the trial period, however, it is capable of sending 2,000 messages each day, which is more than enough to do damage, especially considering that most BEC actors still manually send their BEC emails rather than automating the process. Since April 2019, Agari has conducted more than 200 active engagements with Exaggerated Lion. Its Threat Actor Dossier, which is made available today, documents and analyzes the behaviors and patterns of Exaggerated Lion so that other companies can be aware and protect themselves. The healthcare industry, which has a reputation for being a vulnerable target for cyber attacks, was the top industry exploited by Exaggerated Lion. Other industries of significance targeted were manufacturing, retail, construction and banking. Exaggerated Lion hit target companies in 49 states and the District of Columbia. The only state not targeted by this cybercriminal organization was Nevada. During this engagement Agari identified 48 money mule accounts that were active at various financial institutions. It has worked with law enforcement and banks to help mitigate these accounts that were being used in the money-laundering process. The following statements may be attributed to Crane Hassold, senior director of threat research, Agari: "When you look at the loss numbers, business email compromise (BEC) has a much bigger financial impact than other types of cyber attacks, like ransomware. Recent figures indicate more than $700 million is lost every month to BEC attacks and based on the more recent FBI IC3 report, those numbers are continuing to increase. Exaggerated Lion has built a complex national network of check mules that are key to legitimizing ill-gotten gains from their BEC email attacks. BEC scams are a huge threat to fostering legitimate commerce, and as an industry, we need to be driving more awareness about this issue to keep it front and center in the marketplace." Download the full threat actor dossier to read more. Refer to the blog for additional insights. Register for the upcoming webinar about Exaggerated Lion. About Agari Agari is the market share leader in phishing defense solutions for the enterprise. Through applied science, the Agari Identity Graph™ delivers valuable business context to every email risk decision. Agari ensures outbound email from the enterprise cannot be spoofed, increasing deliverability and preserving brand integrity. It also protects the workforce from devastating inbound BEC, VEC, spearphishing, and account takeover-based attacks, reducing business risk and restoring trust to the inbox. Learn more at agari.com. Media Contact
SOURCE Agari 
|